[CTF] WU - A Compressed File Really ?
CTF InterCampus Ynov 2024
Difficulty Level : Easy
Challenge Category : Web
Description :
Explore this server. It seems to indicate a clue to a particular wrapper... Could this be a way of uncovering something hidden? It's up to you to find out!
Solution Steps
Step 1: Initial Observations
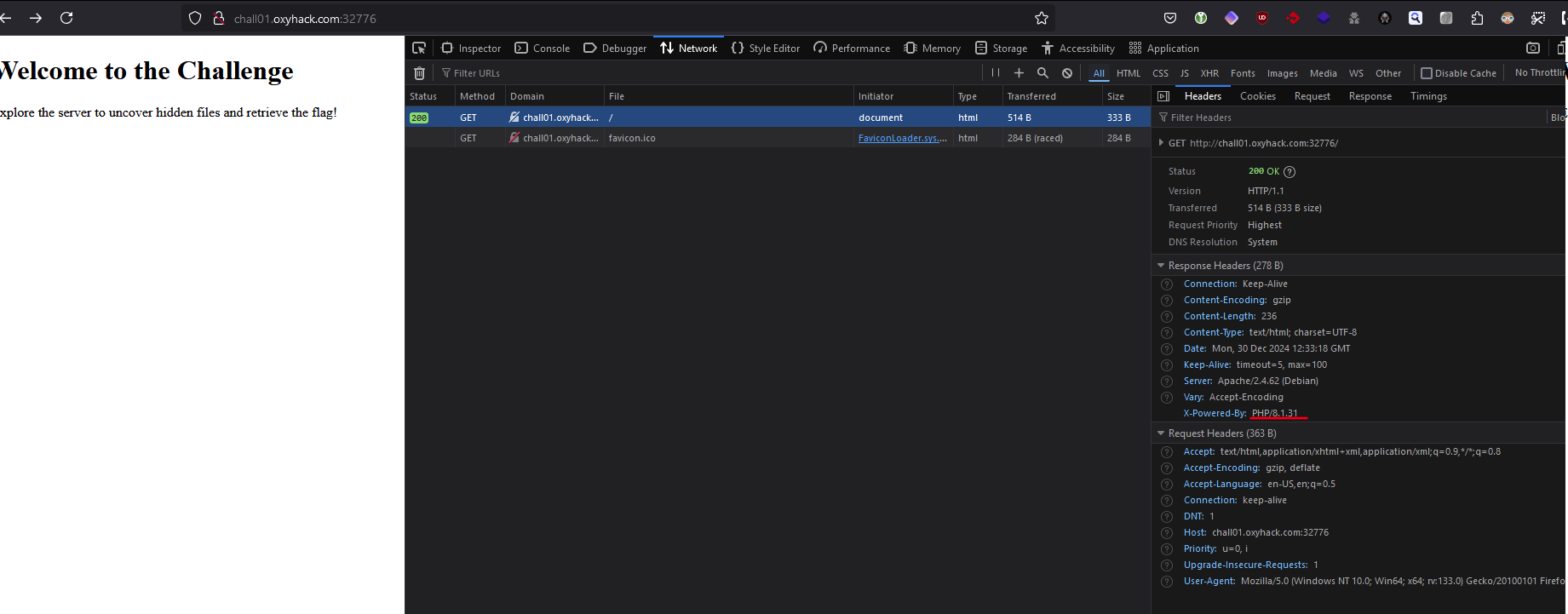
- Upon exploring the server and inspecting the HTTP response headers, we observed that the backend is powered by PHP 8.1.31.
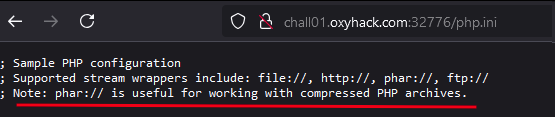
- Accessing
/php.inirevealed supported PHP stream wrappers, including:- phar://: A stream wrapper used to interact with Phar archives, which may store hidden metadata.
Step 2: Enumerating the Server
Using enumeration techniques, we discovered an accessible .phar file at:
/flag.phar
Downloading the .phar File
The .phar file was downloaded locally using the following command:
wget http://chall01.oxyhack.com:32776/flag.phar
This saved the file as flag.phar for further analysis.
Step 3: Accessing Phar Metadata
The metadata of a .phar file can store hidden information, such as flags. To extract this data, we wrote a simple PHP script using the Phar class.
Script: exploit.php
<?php
// Path to the phar file
$pharPath = 'phar://flag.phar';
// Access the metadata of the phar file
try {
// Create a Phar object pointing to the specified file
$phar = new Phar($pharPath);
// Retrieve the metadata stored in the phar file
$flag = $phar->getMetadata();
// Print the flag
echo "Flag: $flag\n";
} catch (Exception $e) {
// Print an error message in case of failure
echo "Error: " . $e->getMessage() . "\n";
}
?>
Step 4: Executing the Script
- Save the script as
exploit.php. - Execute the script using the PHP CLI:
php exploit.php
Step 5: Output
The script successfully extracted the metadata, revealing the hidden flag:
Flag: FLAG{ph4r_wr4pp3r_3xpl01t4t10n}