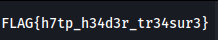
[CTF] WU - Fragmented Flag
CTF InterCampus Ynov 2024
Difficulty Level : Easy
Challenge Category : Forensics
Description :
Fragments of information traverse the web, scattered across a digital trail of requests and replies. Hidden within this exchange lies the answer you seek, but it is not whole.
Solution Steps
Step 1: Analyze the PCAP File with Wireshark
Open the provided challenge.pcap file using Wireshark. In Wireshark:
- Inspect the captured traffic and focus on HTTP requests and responses.
- Look for anomalies or patterns in the HTTP responses that might indicate the presence of the flag.
Step 2: Automate Analysis with TShark
TShark, the command-line version of Wireshark, can streamline the process of analyzing the PCAP file.
Extract HTTP Responses
Run the following command to list all HTTP response frames:
tshark -r challenge.pcap -Y "http.response" -T fields -e frame
Identify Anomalies in Response Sizes
- Look for frames with differences in size or unusual patterns in the data.
- In this case, frame 242 stands out as containing a relevant response.
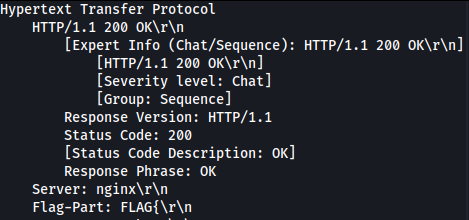
Step 3: Extract Flag Fragments
Run the following TShark command to filter responses containing Flag-Part:
tshark -r challenge.pcap -Y "http.response" -T fields -e http.response.line | grep "Flag-Part"
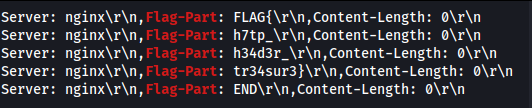
Step 4: Reconstruct the Flag
Use the following pipeline to clean and concatenate the flag fragments into the complete flag:
tshark -r challenge.pcap -Y "http.response" -T fields -e http.response.line | \
grep "Flag-Part" | \
sed -n 's/.*Flag-Part: \([^,]*\),.*$/\1/p' | \
sed 's/\\r\\n//g' | \
sed 's/END//g' | \
paste -sd ''