[CTF] WU - G(F(1)+2)
CTF InterCampus Ynov 2024
Difficulty Level : Hard
Challenge Category : Forensics
Description :
Can you imagine that My friend lived 92 years but his dad lived just lived 64 years, you think its impossible but unfortunately its not.
Scenario:
The challenge begins with a cryptic description about a father living "64 years" and a son living "92 years." After analyzing the context, it becomes clear that these numbers represent encryption methods rather than literal years of age:
- The son (92 years) is encrypted with Base92.
- The father (64 years) is encrypted with Base64.
We are tasked with decrypting the files and following clues to uncover the flag.
Solution Steps
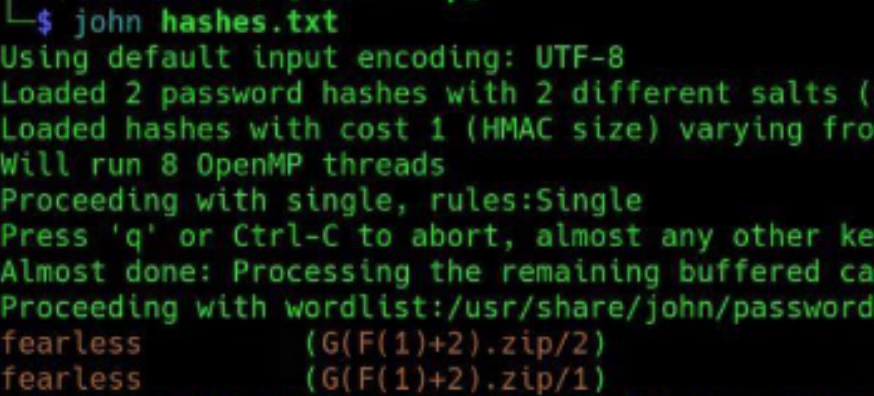
Step 0: Crack the ZIP Password
The provided ZIP file is password-protected. We used John the Ripper with its built-in wordlist to crack the password.
Extract the hash:
Use zip2john to extract the password hash from the ZIP file:
zip2john challenge.zip > zip_hash.txt
Crack the hash:
Use John the Ripper to find the password:
john zip_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Password Found:
The ZIP file's password is successfully cracked, and we extract two files:
- 1.txt (encrypted with Base92)
- 2.txt (encrypted with Base64)
Step 1: Understanding the Files
Upon extracting the ZIP file, we find two text files:
- File 1 (1.txt): Contains text encrypted with Base92.
- File 2 (2.txt): Contains text encrypted with Base64.
After carefully reading the challenge description, we realize the "years lived" metaphor relates to the encryption methods:
- File 1.txt must first be decrypted using Base92 (the child’s method).
- The output from 1.txt must then be combined with 2.txt, and both must be decrypted together using Base64 (the parent’s method).
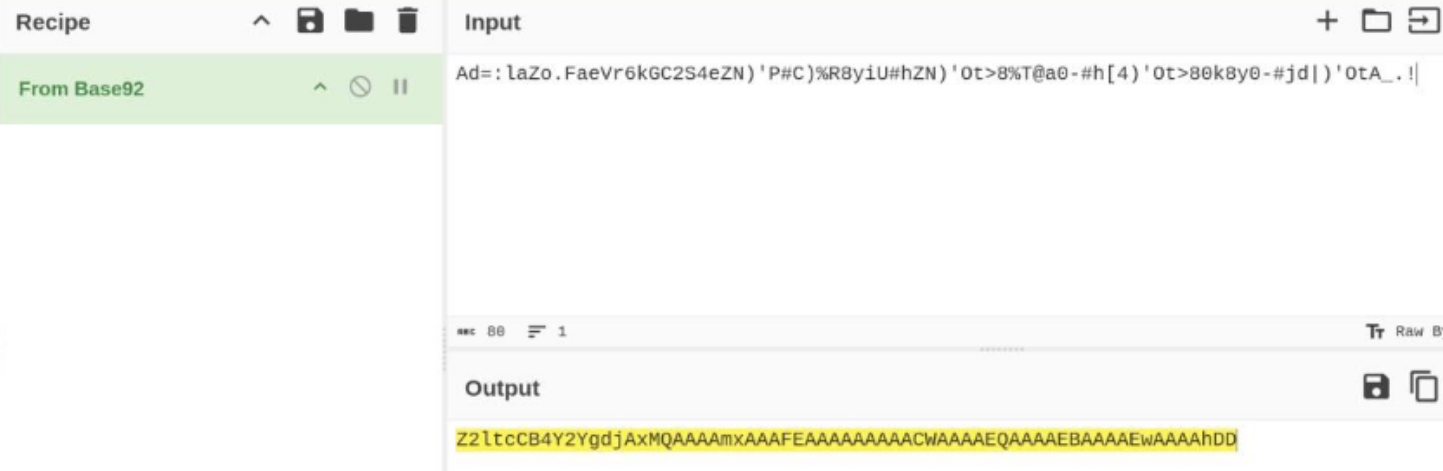
Step 2: Decrypt File 1
- Use Base92 to decrypt 1.txt.
- The output is plaintext data that will later be combined with 2.txt.
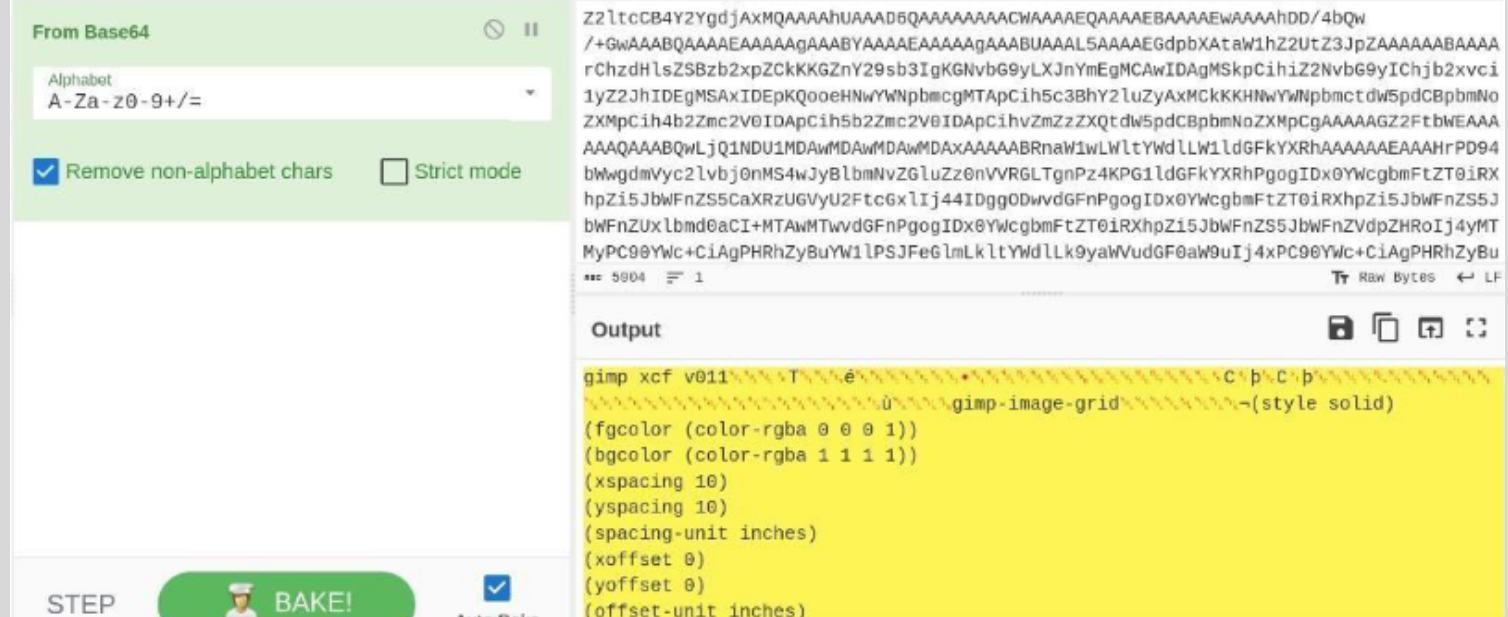
Step 3: Combine and Decrypt File 2
- Append the decrypted contents of 1.txt to the contents of 2.txt.
- Decode the combined file using Base64.
Step 4: Analyze the Decrypted File
The combined file decodes into a GIMP XCF file, a file type used for image editing.
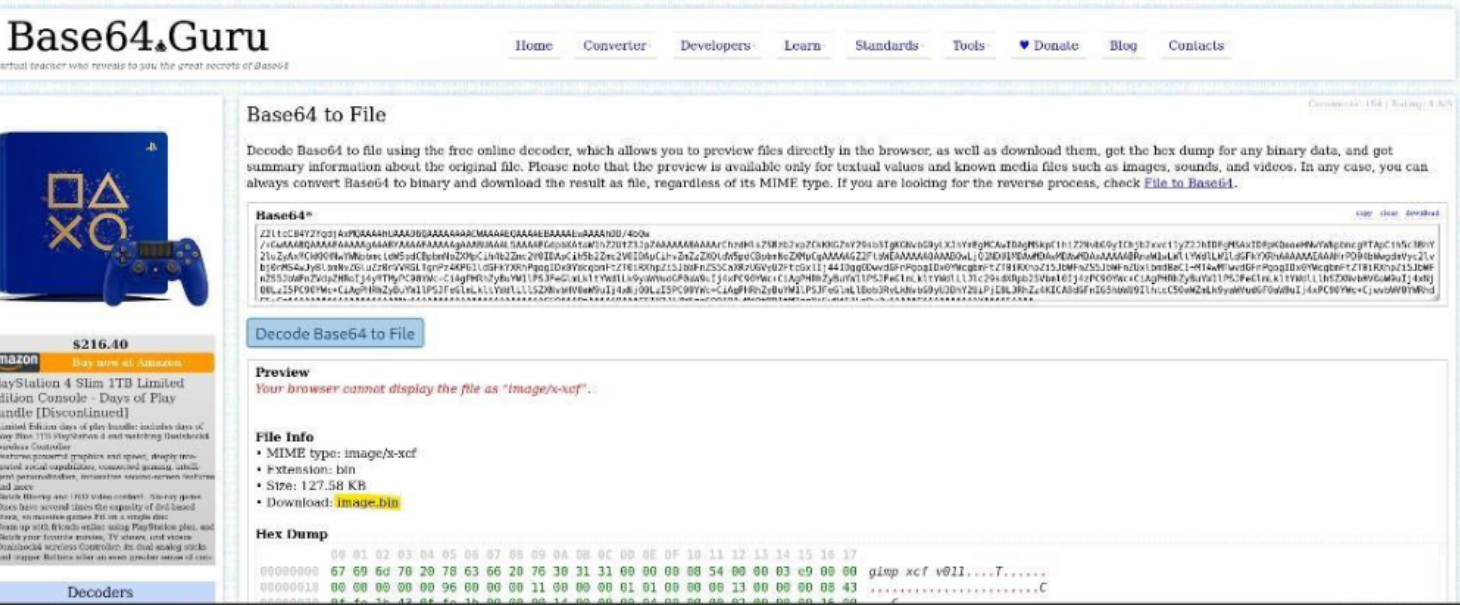
- Open the XCF file using GIMP.
- Adjust the Exposure to
10.00.- This reveals hidden text within the image.
Hidden Text Discovered:
The text contains a URL leading to a MEGA file.

Step 5: Analyze the MEGA File
- Download the MEGA file, which is a Wireshark PCAP file.
- Open the PCAP file using Wireshark.
- Filter for
httppackets:http.request - Look for username and password fields:
- The username is found in one HTTP request.
- The password is sent character-by-character across multiple HTTP requests.
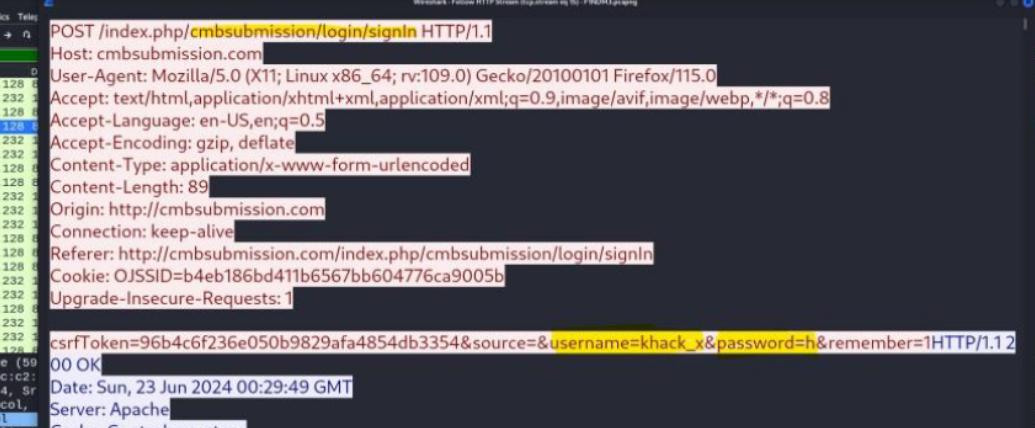
Step 6: Extract the Credentials
After gathering and combining the data from the PCAP file:
- Username:
khack_x - Password:
howtohack
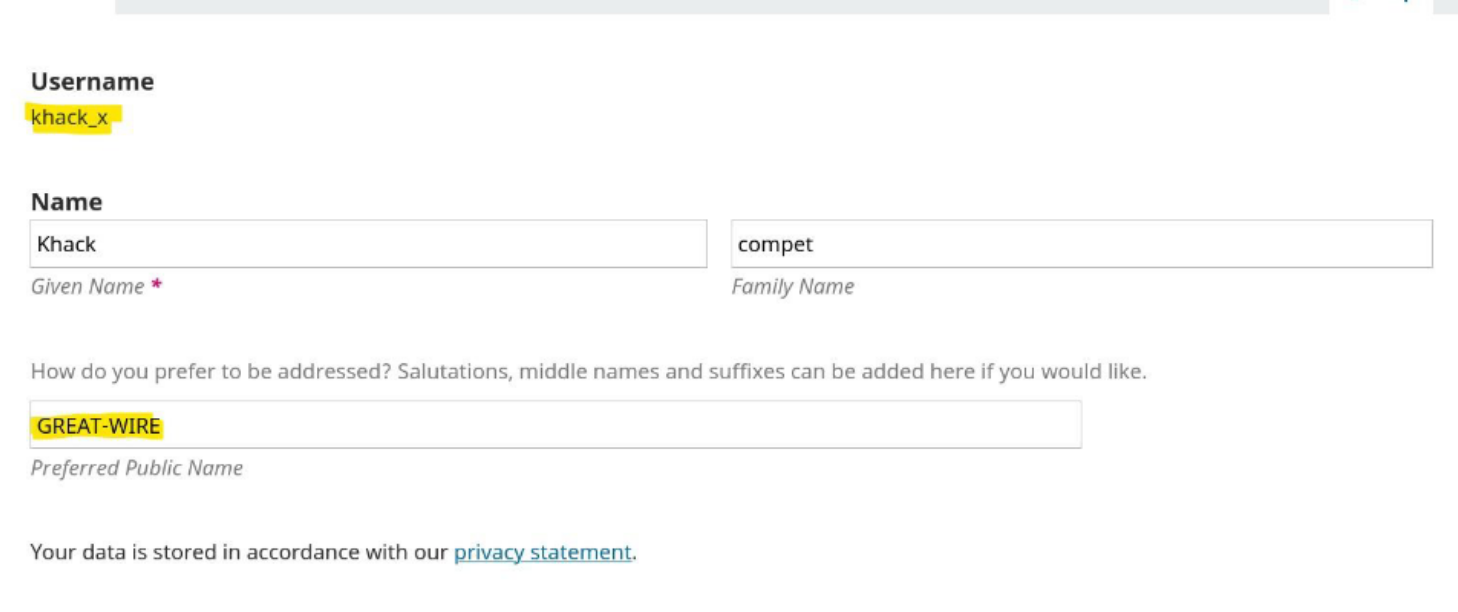
Step 7: Login and Gather Additional Details
- Use the extracted credentials to log in to the provided web application.
- Collect additional public details displayed after login:
- Public Name:
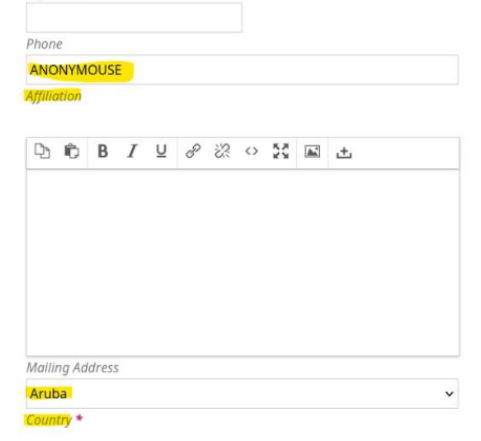
GREAT-WIRE - Affiliation:
ANNONYMOUSE - Country:
ARUBA
- Public Name:
So the flag is :
FLAG{khack_x_howtohack_GREAT-WIRE_ANONYMOUSE_ Aruba}