[CTF] WU - The footprint of danger
CTF InterCampus Ynov 2024
Difficulty Level : Very Easy
Challenge Category : Malware
Description :
A suspicious file has been found, but all that's left of it is its hash. Can you use this information to find the file in the database and collect details about it?
hash: c0202cf6aeab8437c638533d14563d35
flag format : FLAG{nom_du_fichier_nom_du_malware_type_date_de_soumission}
DATE : AAAA-MM-DD Nom du fichier à mettre avec extension.
Solution Steps
Step 1: Analyze the Provided Hash
- The given hash is:
c0202cf6aeab8437c638533d14563d35 - This is an MD5 hash, commonly used for uniquely identifying files.
Step 2: Search for the Hash
Use an online malware database like VirusTotal to search for the hash.
Steps:
- Visit VirusTotal.
- Input the hash
c0202cf6aeab8437c638533d14563d35into the search bar. - Review the search results for details about the file.
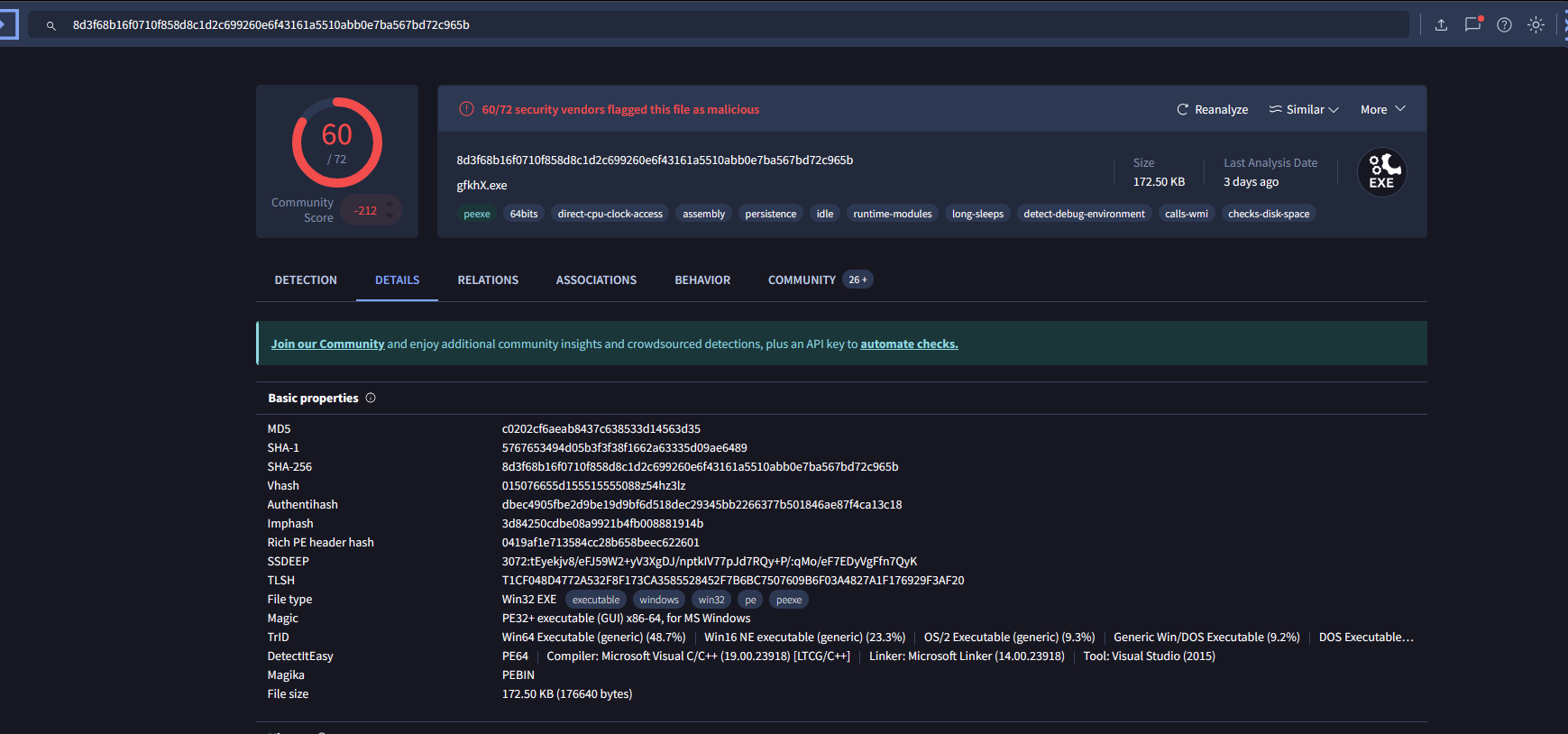
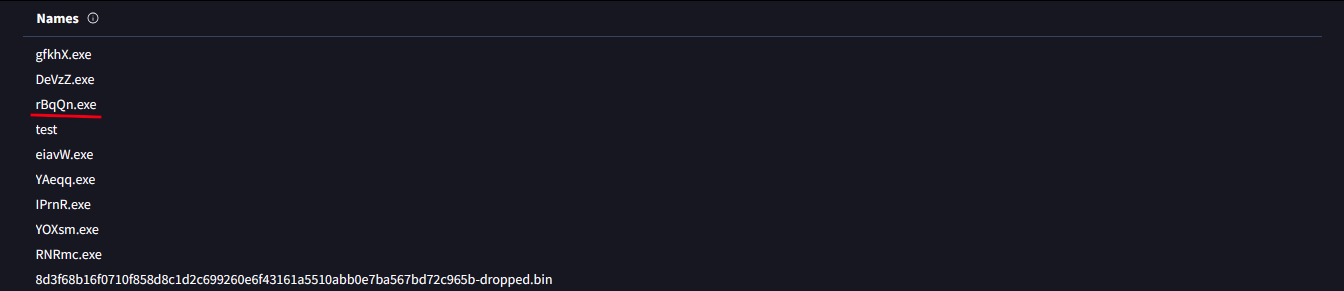
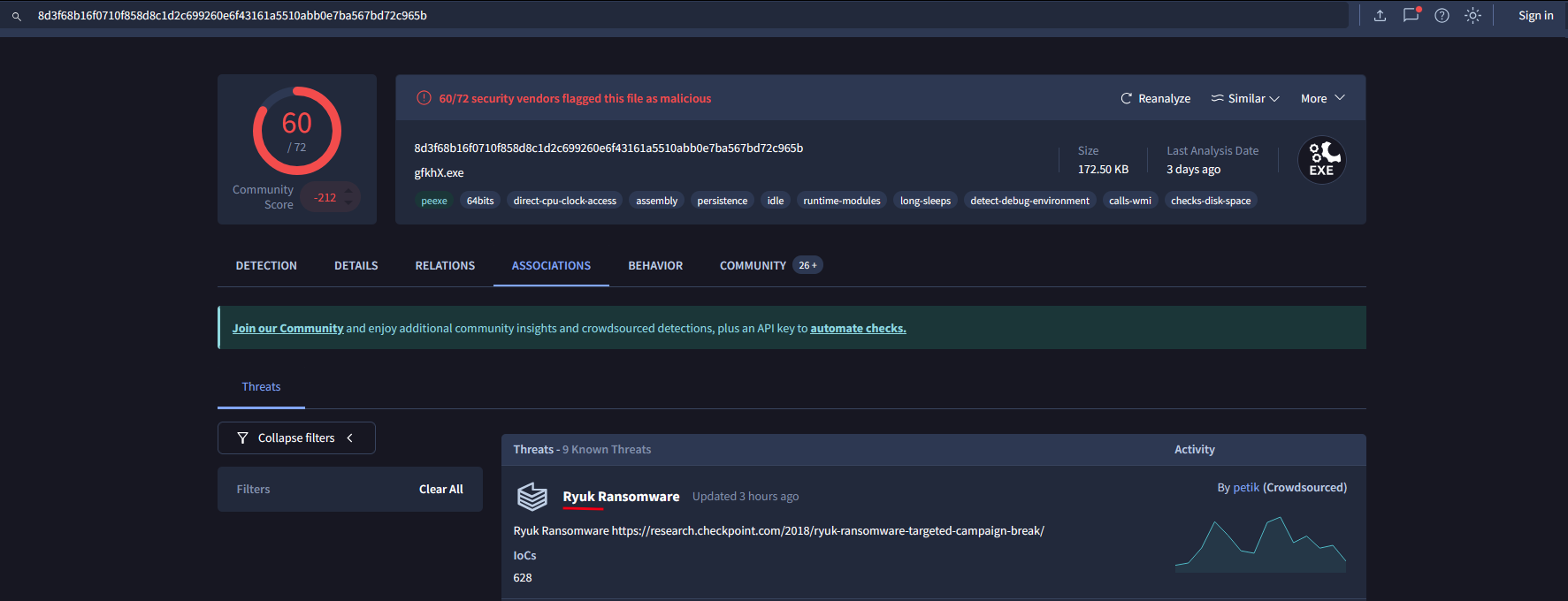
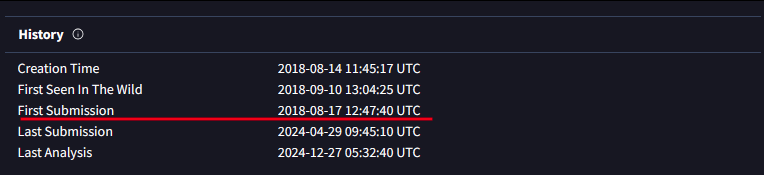
Step 3: Extract Relevant Details
From the VirusTotal search results:
- File Name:
rBqQn.exe - Malware Name:
Ryuk - Type:
Ransomware - Submission Date:
2018-08-17
Step 4: Construct the Flag
The flag format is:
FLAG{file_name_malware_name_type_submission_date}
Using the extracted details:
- File Name:
rBqQn.exe - Malware Name:
Ryuk - Type:
Ransomware - Submission Date:
2018-08-17
Final Flag:
FLAG{rBqQn.exe_ryuk_ransomware_2018-08-17}